overthewire.bandit.lvl[18-19]
Level Goal
the password for the next level is stored in a file readme in the homedirectory. unfortunately, someone has modified .bashrc to log you out when you log in with SSH
Solution
from ssh(1) man page
if command is specified, it is executed on the remote host instead of a login shell.
so, we can cat(1) the readme file, the server will reward us with next level’s password and we are done
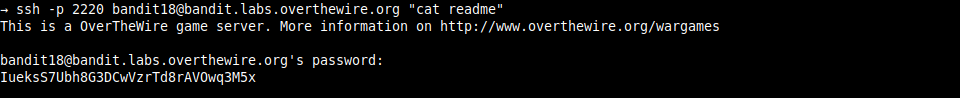
well, now i will demonstrate another way of solving this challenge.
when we connect to the remote server with the ssh client, the ssh daemon that is listening for incoming connections on the remote server will fork a child process, this child process will handle all the processing details for our client login session (creating the pseudoterminal setup, authenticating the user, execute a login shell, etc…).
now we can disable the pseuodterminal allocation and hence no login shell will be executed and connected to the pseuodterminal slave side. the ssh server will execute the commands we pass to it through the TCP socket the same way it did in the first method when we executed only the cat(1) command. we can disable pseudoterminal allocation by specifying the -T option for the ssh client.
now we will use this method to get user bandit19’s password and we are done.